
To Renew or Not Renew, That is the Question
The following items should help you decide how to prepare your hardware for the Windows 10 migration.

The following items should help you decide how to prepare your hardware for the Windows 10 migration.

With Windows 7 end of life quickly approaching, it’s time to start thinking about what needs to be done to prepare.

You’ve all heard the panic. Windows is cutting off support for its widely popular version 7 software.

Essentially, you have two general options when it comes to storing data for your business: the cloud, and local servers.

No matter what industry you’re in, compliance acronyms are abundant, filling your days with both confusion and regulation.

Social engineering cybercriminals use life-like scenarios to prey on every day humans.

These are just a few of the main ways that social engineers are using social media to target people.

With the technology world constantly changing, IT support specialists have to consistently stay on top of their game to deliver results to their clients.

Data breaches can happen in many forms. Some of it is all electronic, and you never know the human behind the mask.
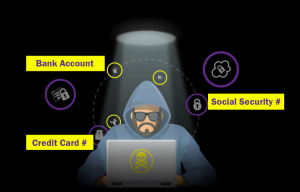
Recent research suggests that credit card data is the most sought after data in a breach. Why is that?

Phishing attempts directed at specific individuals or companies have been termed spear phishing. These are highly targeted attacks.

Malvertising is a cyber threat found in malicious advertising. In this case, hackers use advertising to spread malware.
1730 PARK ST., STE. 115
NAPERVILLE, IL 60563
(630) 282-6540