
Is The Public Cloud Right For Your Business?
Dropbox pioneered cloud-based sharing of consumer photos and files.

Dropbox pioneered cloud-based sharing of consumer photos and files.
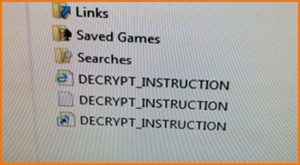
CryptoWall has been out for over a month, and it’s been a devastating virus that will destroy all of your documents.

On April 8, 2014, Microsoft finally ended support on Windows XP.
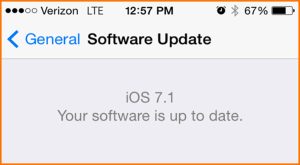
If you have an iOS device, you may have upgraded as soon as your device prompted you to do so.
Whether it’s at home or in our businesses, we can probably all agree that network security is incredibly important.
Businesses today rely on computer technology more than ever to run their business.
The creation of the Internet was the dawn of a new era.
There are plenty of cloud technologies today that can help us with our most critical pieces of data.
Although it doesn’t happen too often, sometimes your iPhone/iPad can get sluggish.
Apple users with the iPhone 4 and iPhone 4S may have experienced an issue after upgrading to iOS 5.0.1.
Our Chicago IT Managed Services team received a call late last night from a CPA working late (it’s tax season).